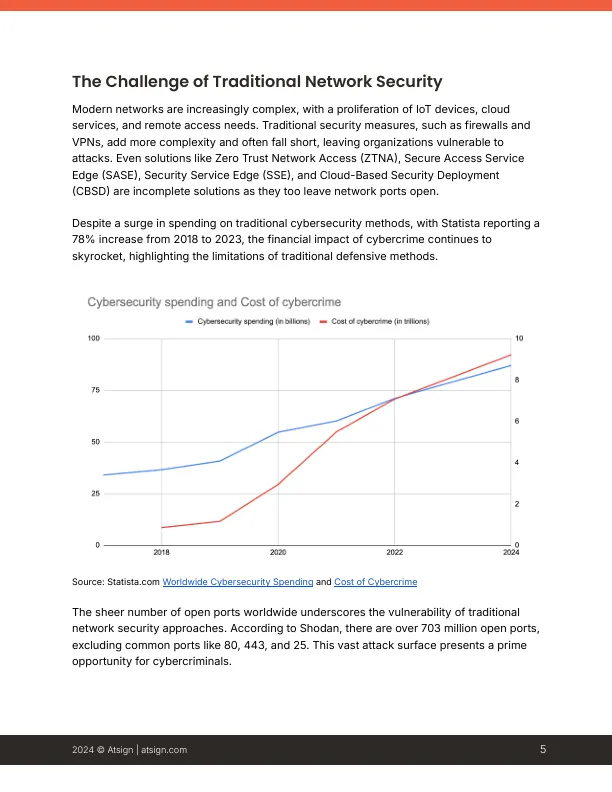
机构名称:
¥ 1.0
Executive Summary 3 The Challenge of Traditional Network Security 5 Atsignʼs NoPorts Approach 6 How it Works 7 Benefits of NoPorts 7 NoPorts: A New Era of Network Security 8 Use Cases 8 Securing Sensitive Data in the Cloud 8 Securing Remote Access for Private 5G Networks 9 Securing AI at the Edge 9 Secure Data Sharing and APIs 9 Appendix - More Technical Detail 10 Atsign Architecture and Components 10 Additional NoPorts Components 10 Zero Trust Framework 11 How it WORKS 11软件安装和密钥管理11连接到ATSERVER 12目录查找12中继设置和安全连接12通过策略引擎12键和加密13封闭端口和攻击表面减少13额外资源:14
用Atsign的零信任方法彻底改变网络安全