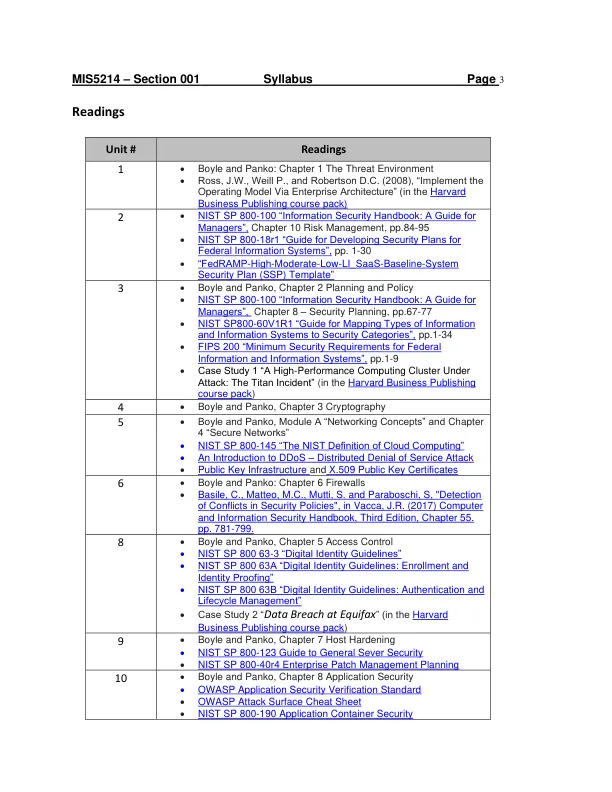
1 • Boyle and Panko: Chapter 1 The Threat Environment • Ross, J.W., Weill P., and Robertson D.C. (2008), “Implement the Operating Model Via Enterprise Architecture” (in the Harvard Business Publishing course pack) 2 • NIST SP 800-100 “Information Security Handbook: A Guide for Managers”, Chapter 10 Risk Management, pp.84-95 • NIST SP 800-18r1 “Guide for Developing Security Plans for Federal Information系统”,pp。1-30•“ FedRamp-High-Mighter-LOW-LI_SAAS-BASELINE-SYSTEM-SERCEMSED SECUREPAND(SSP)模板” 3•Boyle and Panko,第2章规划和政策•NIST SP 800-100“信息安全手册:管理人员指南”,第8章,第8章 - 安全计划,PP.67-77-77-77-77-77-77-77-77-7-7-7-7-77-7-7-7-60-60-60V 1” pp.1-34 • FIPS 200 “Minimum Security Requirements for Federal Information and Information Systems”, pp.1-9 • Case Study 1 “A High-Performance Computing Cluster Under Attack: The Titan Incident” (in the Harvard Business Publishing course pack ) 4 • Boyle and Panko, Chapter 3 Cryptography 5 • Boyle and Panko, Module A “Networking Concepts” and Chapter 4 “Secure Networks” • NIST SP 800-145 “The NIST Definition云计算”•DDOS的简介 - 分布式拒绝服务攻击•公共密钥基础架构和X.509公共钥匙证书6•Boyle和Panko:第6章防火墙•Basile,C.,Matteo,M.C.,Mutti,S。和Paraboschi,S。和Paraboschi,S,“在安全策略中的冲突”,第5章,第5章,第5章,第5章。 pp。781-799。8 • Boyle and Panko, Chapter 5 Access Control • NIST SP 800 63-3 “Digital Identity Guidelines” • NIST SP 800 63A “Digital Identity Guidelines: Enrollment and Identity Proofing” • NIST SP 800 63B “Digital Identity Guidelines: Authentication and Lifecycle Management” • Case Study 2 “ Data Breach at Equifax ” (in the Harvard Business Publishing course pack ) 9 • Boyle and Panko,第7章主机硬化•NIST SP 800-123一般性重复安全指南•NIST SP 800-40R4企业补丁管理管理计划10•Boyle and Panko,第8章应用程序安全•OWASP应用程序安全验证标准标准•OWASP攻击表•NIST SP 800-190应用程序容器安全
MIS 5214 - 安全体系结构春季2025
主要关键词